If you're attempting to use Event Viewer's Security logs to track down logon events and you wish to filter them specifically by username, you can perform the steps below to do this with ease.
Once Event Viewer is running on the Active Directory server, go to the Security logs (under Windows Logs) and select 'Filter Current Log..." on the right hand side.
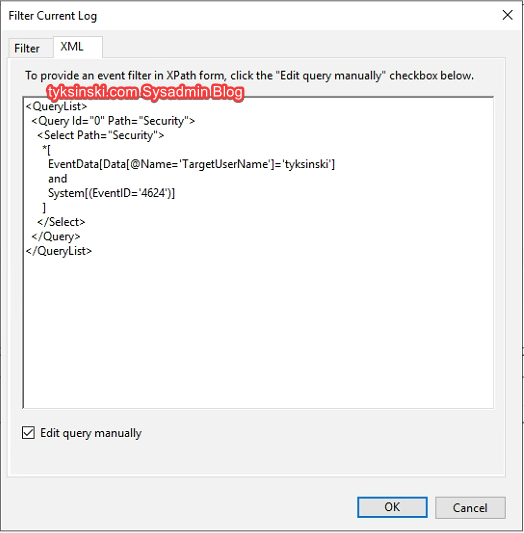
Now go to the XML tab, select 'Edit query manually' and use the query below to filter logon events by a specific username:
<QueryList> <Query Id="0" Path="Security"> <Select Path="Security"> *[ EventData[Data[@Name='TargetUserName']='ReplaceUsername'] and System[(EventID='4624')] ] </Select> </Query> </QueryList>
Make sure to replace the username field with the one you're looking for in the query above.
When all is said and done, your query should look like this before you hit 'OK':
After hitting OK you should see all saved logon events that match the target username.
Please keep in mind that not all logon events are shown by default unless you have previously configured your Event Viewer to a bigger size. The default size of logs does not allow for many events to be saved as they are constantly replaced by new ones.